Not all stories are created equal. That’s why some go viral, while others barely get any likes.
Cyber-attacks are like that. Perhaps you recall a few infamous data breaches of the last few years, like Facebook, Yahoo, Uber, and Cathay Pacific?
Funnily, these are all big names and millions of accounts, emails, and even passport numbers were compromised.
What you probably don’t know is that small businesses face as many as 4000 cyberattacks every day! IBM says that number is 62% of all cyberattacks that occur daily. According to the University of Maryland, there’s a cyberattack every 39 seconds.
Why SMBs? Because they’re soft targets. They don’t have the capabilities (sometimes) nor do they take the precautions to defend themselves.
The 2018 Hiscox Cyber Readiness Report (PDF) that surveyed 4000 organizations in the US, UK, and Europe found that 73% of the companies weren’t ready to respond to a cyberattack.
There’s a grimmer fact. The US National Cyber Security Alliance says that 60% of small businesses that have faced such attacks close down within six months.
If your small business were to be compromised, chances are no one would hear about it on the evening news. Nevertheless, it could cost you some $700K and have other, worse consequences.
What makes today’s small businesses even more vulnerable is that it’s not a contained unit that operates from a single office. It’s a distributed structure with remote members placed worldwide.
That’s a very good thing, as we say. But it does mean you need to be better prepared to defend your business.
And to help your remote business do just that, we’re delving into the topic of cybersecurity. In today’s article, we’re talking about attacks to which your distributed team may be vulnerable, why that may be the case, and what you can do about it.
In our next article of this series, we’ll outline a data security plan that you can implement in your business and protect your company from any cyberattacks.
Top reasons, problems, and sources of cyberattacks
While cyberattacks may occur due to human or technical error, they are mostly perpetrated with criminal intent.
For a small business that could mean many problems, like:
- the attacker wants user information including credit card
- access to intellectual property and internal memos
- steal employee information to commit health insurance or tax fraud
- flood or slowdown or disrupt systems which will lead to loss of business – 76% of attacks have financial intent
- the attacker is working on behalf of the competition
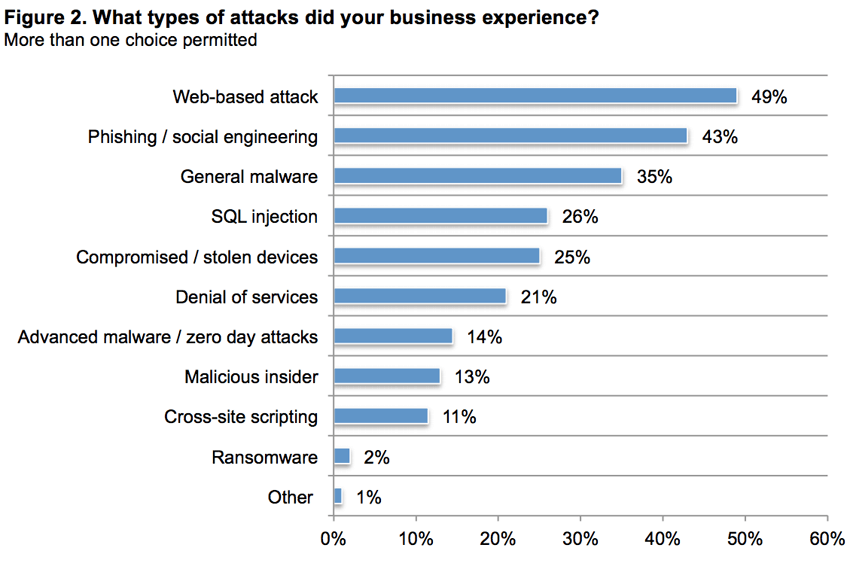
Cyberattacks can take many forms and have many consequences. Some of the most common cyberattacks of the past few years have been:
- Phishing and spear-phishing – this accounts for most cyberattacks
- Malware attack – 58% of these attacks target SMBs
- Eavesdropping attack
- Denial-of-Service
- SQL injection attack
You can get a more detailed list of the types of attacks and their explanations here.
Cybercriminals can exploit any weakness in your distributed systems to carry out attacks, but the top sources of attacks are:
- Unknown emails and attachments (especially files with MS Office extensions) – 92% of malware come via emails
- Mobile malware – these attacks are on the rise and grew 54% in 2017
- Grayware (appears to be safe but shares private info) and third-party apps (99.9% of mobile malware comes from these)
- Unsecured employee devices connected to the company network
- IoT devices – these are easier to breach and connect to a bigger system

Exactly which sort of attacks your business is susceptible to depends on your business, systems, products, employees, where you operate and so on.
You’re more at risk when your business has something an attacker would want, or you have some obvious flaws in your system, such as when you:
- Collect and store customer data like name, email, phone number, billing address
- Don’t upgrade the software you use (only 38% of SMBs regularly do)
- Don’t encrypt databases
- Don’t monitor company credit card or other spending reports
- Don’t follow a companywide password standard
- Don’t have cyber risk insurance
To get a better handle, you should conduct a cyber risk assessment. Here’s a free checklist that can help you.
The result of the risk assessment will play an essential role in crafting your data security plan that we’ll share with you in the next article. Stay tuned for that.
Remote employee cybersecurity know-hows and policies
If your employees aren’t following through on the security measures you’ve implemented, your efforts will become moot. So, here are a few points to help reinforce your cybersecurity plan:
- Create and share a remote cybersecurity policy that is strictly maintained, no matter where anyone is located.
- Orient all employees in these policies during the onboarding process. Plus, regularly update your team’s knowledge by participating in webinars from institutions like the National Cyber Security Alliance’s (NCSA’s) CyberSecure My Business™.
- All remote employee devices should have the same (level of) security measures installed. Otherwise, they should be blocked.
- Either give your remote workers a laptop when you hire them or insist they separate their work laptop from a personal one. And let your company have some administrative privileges on the work laptop.
- Ban USB drive and flash media from accessing the work laptop. Here’s how.
- Emails are a major source of malware. One criterion you could set would be that emails from unknown sources with attachments are automatically sent to spam/blocked. Also, encrypt emails that you send to employees.
- Use remote monitoring and management (RMM) app to see who is using which tool, and monitor and trace work data. If someone is copying data out of the system without legitimate reason – that should raise a flag. If that seems invasive, remember that remote IT management is an emerging trend growing alongside remote work.
- Outline what details of live projects they are allowed or not allowed to share on social media – as that’s another way to invite cybercriminals.
- In weekly meetings, send your team reminders of security measures easily forgotten – like update security patches, don’t use public Wi-Fi.
- Make it mandatory for remote employees to immediately inform you/IT department if there’s a breach on their device.
Lastly, hire employees who will follow through on organizational policies. Our remote developers are pros who understand the importance of cybersecurity. Call us to learn more.




