Application Security (AppSec) applies security best practices to software applications, while DevSecOps is a cultural mindset that integrates security into the entire CI/CD pipeline from the outset. Therefore, AppSec vs DevOps are actually not in a fight for dominance but in a tango.
AppSec and DevSecOps are two complementary approaches to building secure software, operating at different levels and in various ways. Understanding their differences is crucial for risk management, ensuring compliance, and achieving governance goals.
Here we will explore both approaches, contrasting their goals and methods to offer strategic insights on integrating or prioritizing AppSec and DevSecOps in your company.
What is Application Security (AppSec)?
AppSec is the set of practices, techniques, and tools focused on protecting software against threats and vulnerabilities. It focuses primarily on the application itself, the source code, configurations, and security requirements.
AppSec Goal
The goal is to identify, correct, and prevent security flaws in the software.
AppSec Tools
AppSec tools find and mitigate vulnerabilities within the application itself: its code, dependencies, and configuration. These tools are often integrated into the Development and Testing phases of the SDLC, supporting the “Shift Left” security approach.
Static Application Security Testing (SAST)
SAST analyzes source code or bytecode (without execution) to identify security flaws such as buffer overflows, injection flaws, and insecure coding practices.
Dynamic Application Security Testing (DAST)
Tests a running application (black-box) by simulating attacks to find runtime vulnerabilities like cross-site scripting (XSS), misconfigurations, and authentication flaws.
Software Composition Analysis (SCA)
Scans for known vulnerabilities, license risks, and health issues in open-source and third-party components (dependencies).
Interactive Application Security Testing (IAST)
Combines aspects of SAST and DAST, monitoring application behavior from within during running/testing to find vulnerabilities with high context and accuracy.
Secrets Detection
Scans repositories, files, and histories to find hardcoded credentials, API keys, tokens, and other sensitive information.
Application Security Posture Management (ASPM)
Unifies findings from various security tools (SAST, DAST, SCA) into a single view, prioritizes risks, and manages the overall application security program.
| Tool Category | Tool/Platform Examples | SDLC Phase |
| Static Application Security Testing (SAST) | Semgrep, Checkmarx, OpenText Static Application Security Testing (SAST), Snyk Code, Coverity, SpotBugs (with FindSecBugs) | Coding, Development |
| Dynamic Application Security Testing (DAST) | Burp Suite Professional, OpenText Dynamic Application Security Testing (DAST), Snyk API & Web, ZAP (Zed Attack Proxy) | Testing, Runtime |
| Software Composition Analysis (SCA) | Snyk Open Source, Black Duck SCA, OSV Scanner, OpenText Core Software Composition Analysis, Dependency-Check | Coding, Development, Testing |
| Interactive Application Security Testing (IAST) | Often integrated into AppSec platforms | Testing, Runtime |
| Secrets Detection | GitGuardian, Gitleaks, TruffleHog, Yelp/detect-secrets | Coding, Development |
| Application Security Posture Management (ASPM) | Jit, Cycode, Black Duck Polaris™ Platform | Management, Continuous Monitoring |
What is DevSecOps?
DevSecOps is an extension of DevOps, incorporating security (“Sec”) to create a secure, continuous software development lifecycle (Secure SDLC, S-SDLC). Here, the focus is on the process and culture of software development and delivery. DevSecOps ensures that security is a shared responsibility across the entire team (developers, operations, and security) from the start (“shift left”).
DevSecOps Goal
The idea behind DevSecOps is to accelerate software delivery, maintaining a high level of security in the CI/CD pipeline.
DevSecOps Tools
DevSecOps leverages all the tools AppSec does, but integrates them into the continuous integration/continuous delivery (CI/CD) pipeline and often uses additional tools geared towards automation and scalability. Their security best practices extend beyond the application code to secure the infrastructure, containers, pipeline, and runtime environment.
CI/CD Pipeline Integration & Orchestration
Automates the build, test, and deployment process, acting as the central hub to integrate all other security scanning tools.
Infrastructure as Code (IaC) Security
Scans configuration files (e.g., Terraform, Kubernetes, CloudFormation) for security misconfigurations and policy violations before deployment.
Container & Image Scanning
Scans Docker images and container registries for known OS and application vulnerabilities and compliance issues.
Secrets Management
Securely stores and manages sensitive credentials (keys, tokens, certificates) separate from the codebase, and dynamically generates them at runtime.
Runtime Security & Monitoring
Provides real-time threat detection, behavioral analysis, and response capabilities for running applications and cloud workloads (often focused on containers/Kubernetes).
Security Information and Event Management (SIEM) / Observability
Collects, aggregates, and analyzes security data and logs from all tools and environments for threat detection, compliance, and incident response.
| Tool Category | Tool/Platform Examples | SDLC Phase |
| CI/CD Pipeline Integration & Orchestration | Jenkins, GitLab CI/CD, GitHub Actions, Atlassian Pipelines (Bitbucket) | Build, Test, Deployment |
| Infrastructure as Code (IaC) Security | KICS, Checkov, Terrascan, Snyk Infrastructure as Code | Development, Deployment (Provisioning) |
| Container & Image Scanning | Trivy, Anchore, Grype, Clair, Snyk Container | Development, Build, Runtime |
| Secrets Management | Azure Key Vault, HashiCorp Vault | Deployment, Operations |
| Runtime Security & Monitoring | Falco, Tetragon, Microsoft Defender for Cloud, Datadog Security Monitoring, Azure Monitor | Operations, Monitoring |
| Security Information and Event Management (SIEM) / Observability | Datadog, Splunk, Microsoft Sentinel | Operations, Monitoring |
Difference between AppSec vs DevSecOps
DevSecOps uses and automates AppSec practices and applies them within a broader cultural and procedural context. It ensures that AppSec moves from the end of the development cycle to be a continuous and integral part of all stages.
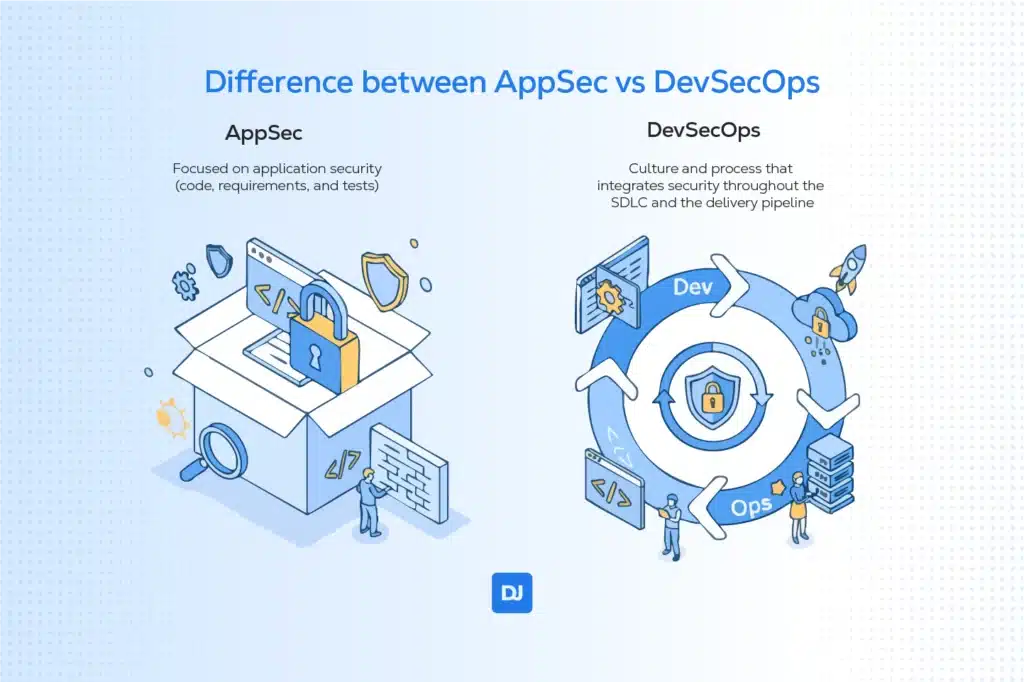
| AppSec (Application Security) | DevSecOps | |
| Scope | Focused on application security (code, requirements, and tests). | Culture and process that integrates security throughout the SDLC and the delivery pipeline. |
| Approach | Technical security discipline (what and how of app security). | Operational methodology (where and when security is integrated). |
| Culture | It may be a separate team or process (silo). | Promotes collaboration and shared responsibility between Dev, Sec, and Ops. |
| Automation | May use automation (e.g., SAST), but it is not necessarily continuous and integrated. | Strong emphasis on automation and continuity of security in the CI/CD pipeline. |
How Each Fits into the Software Development Lifecycle (SDLC)
In a waterfall software development lifecycle, AppSec activities correspond to specific phases. In Agile, DevSecOps essentially intertwines with AppSec. It brings security into every stage of the pipeline in an automated and ongoing way.
AppSec in Waterfall
For example, in the planning/design phase, AppSec might involve defining security requirements and threat modeling (ensuring the design addresses security from the start). During implementation, AppSec means developers follow secure coding guidelines and perhaps use security-focused IDE plugins or pre-commit hooks to catch issues early.
In the testing phase, dedicated security testing occurs, such as static code analysis, dynamic testing, and penetration testing, to catch vulnerabilities before release. Finally, before deployment, there may be a formal security review or risk sign-off by the security team. This classic approach sometimes led to a scenario where “development is done, now let’s do a security review”. If that review finds major issues, it can delay release while developers go back and fix problems.
AppSec in Agile development
Modern AppSec practices try to engage earlier, but the integration is often not seamless. It might rely on handoffs between teams. From a lifecycle perspective, AppSec ensures that at each major stage (design, coding, testing, deployment) there are security checkpoints. However, those checkpoints can be time-consuming gates, which is why DevSecOps, together with AppSec, evolved to improve the process.
DevSecOps and AppSec
DevSecOps shifts the mindset to continuous improvement. With DevSecOps, security is an ongoing thread in the SDLC, which results in a more collaborative and efficient approach. Developers fix security issues as they code (with immediate feedback from tools), rather than a big list of findings at the end. Moreover, the feedback loop for security is much faster, minutes or hours (from an automated tool) rather than days or weeks (from an external penetration test report). However, this doesn’t mean DevSecOps dismisses pentests; it only brings more security tests and more often.
In short, AppSec activities map to specific SDLC phases, whereas DevSecOps blends security into every phase of the SDLC. DevSecOps treats security as a continual process, aligning with Agile/DevOps continuous integration and delivery practices. This alignment helps avoid the late-stage scramble to fix issues, thus supporting both security and speed.
Impact on Risk Management and Compliance
AppSec reduces risk and supports compliance on a per-application basis. DevSecOps broadens and automates risk management and compliance across the development process, aiming for real-time risk reduction and “baked-in” compliance. Companies that effectively implement both will see that AppSec provides the expertise and controls to meet standards (like PCI DSS, NIST, GDPR), while DevSecOps provides the mechanisms to enforce those controls continuously without slowing down development.
Risk Management with AppSec
AppSec reduces the technical risk in software by fixing security gaps. It identifies specific risks and mitigates them by conducting thorough vulnerability assessments, penetration tests, and code reviews.
The approach is “find the vulnerability, fix it”, thus reducing risk item by item. AppSec teams maintain a risk register or vulnerability tracker for applications and work with product owners to prioritize fixes based on severity and impact.
This approach ensures that known issues are addressed before release, thereby lowering the likelihood of breaches. Additionally, because AppSec focuses on known best practices (like OWASP Top 10, etc.), it helps manage risk by building security in from the start.
However, a limitation of a standalone AppSec approach can be the timing. If risks are identified late, the cost and impact of fixing them are higher, and if not all apps are thoroughly reviewed, something might slip through.
Risk Management with DevSecOps
DevSecOps enhances risk management by making it continuous and adaptive. It catches emerging risks faster by integrating security scanning and monitoring throughout the pipeline.
For example, if a new critical CVE (common vulnerability/exposure) is announced, an integrated SCA tool can immediately flag which applications are affected via their dependencies. This continuous approach means your risk posture is always up-to-date with the latest code and threat information.
DevSecOps also broadens the scope of risk management beyond just the application code.
It looks at risks in:
- deployment (misconfigurations, open ports),
- infrastructure (unpatched servers, insecure container images),
- processes (lack of visibility or slow response)
DevSecOps provides a more holistic risk management, since security is at every step of the SDLC. It transforms the security model from reactive to proactive, identifying and addressing security risks earlier while maintaining development speed.
Compliance in AppSec
AppSec programs align with meeting specific compliance or regulatory requirements. For example, an application handling payments must comply with PCI DSS, which has detailed requirements for code reviews, penetration testing, and secure development practices.
An AppSec team will ensure those activities are done and documented to satisfy compliance audits. AppSec provides the tools and frameworks to meet regulations, such as secure coding standards for GDPR data protection, or audit logs to meet SOC 2 controls.
In many cases, compliance checklists map well to AppSec tasks, so having a strong AppSec program helps tick those boxes. However, compliance activities can become periodic and checklist-driven, which sometimes leads to a “point-in-time” security stance. I mean, the app’s safe at audit time, but what about 6 months later?
Compliance in DevSecOps
DevSecOps aims to ensure continuous compliance. Instead of treating compliance as a separate audit exercise, DevSecOps builds compliance checks into the pipeline.
For instance, if a policy says all web traffic must be encrypted, a DevSecOps pipeline can have an automated test that any new configuration has HTTPS enabled; rebuking the build if not. Compliance violations are caught immediately, not just during an annual review.
DevSecOps can also produce evidence for auditors more easily: since everything is automated and logged, you can show reports of all security scans, configurations, and test results for each release.
Many companies adopting DevSecOps use the concept of Compliance as Code: encoding regulatory requirements into scripts and tests. Compliance is continuously enforced in the same way code quality is. Essentially, DevSecOps operationalizes compliance: if done well, you are always compliant because any non-compliant change would be caught by the pipeline controls.
Impact on Delivery Speed and Agility
AppSec, when bolted on at the end, can slow down delivery, but it secures the application; DevSecOps aims to secure the application and speed up delivery by making security an integrated part of the workflow. Companies applying DevSecOps deploy faster than before, because fewer last-minute issues arise and teams spend less time going back to fix security problems discovered out of band.
AppSec’s Impact on Speed
Traditional AppSec measures, if not well-integrated, can introduce delays. For example, a security review phase might mean that after developers finish coding, they must wait perhaps days or weeks for a security team to test and sign off on the release.
If that review finds issues, going back to fix them and retest can further delay deployment. Security bottlenecks are a known pain point; a thorough penetration test could take multiple weeks, during which a feature cannot launch if it’s gated by that test.
Moreover, developers might context-switch away and then come back to fix issues later, which is less efficient. That said, a mature AppSec program can mitigate some delays by engaging early (like having security requirements from the start and doing some parallel testing).
But generally, when security is a separate step, it’s perceived as something that can slow down projects if not planned carefully. That being said, including AppSec practices in a DevOps model isn’t automatic. Therefore, if done naively, you could end up with just adding more work to developers without streamlining it.
DevSecOps’s Impact on Speed
DevSecOps balances security with speed. By automating security checks and integrating them into the fast feedback loops of CI/CD, DevSecOps can actually increase development speed without sacrificing security.
For example, instead of waiting for a separate scan, developers get immediate feedback from automated tools, which can be faster to address (fixing a vulnerability when the code is fresh in mind) and avoids long delays later.
DevSecOps encourages building “secure by default” pipelines, so the act of deploying software includes security by nature, rather than being an added hurdle. The result is that teams can release more frequently with confidence.
When security checks are scripted and run in minutes, they become just another part of the build, not a roadblock. Additionally, by catching issues early, DevSecOps avoids the scenario of late-stage surprises that cause emergency rework (a big schedule disruptor).
Choosing to Invest Between AppSec vs DevSecOps
Investing in AppSec and DevSecOps is not a question of opting between AppSec or DevSecOps, but rather how to balance and sequence investments in both. For example, if your organization’s developers and security staff don’t already have good habits in secure coding and vulnerability management, jumping straight to DevSecOps automation could result in false confidence.
AppSec as the Foundation, DevSecOps as the Enabler
DevSecOps cannot succeed without solid AppSec practices underpinning it. It’s advisable to start an initial investment in AppSec basics: training developers in security, establishing secure coding standards, and acquiring essential testing tools. These AppSec fundamentals provide the foundation for any future advanced DevSecOps program.
For example, first hire an AppSec engineer or consulting firm to set up a SAST/DAST toolchain and to train the dev team. Once the team knows how to code securely and handle scan results, you can then integrate those tools into CI/CD and scale up automation (the DevSecOps part).
Maturity and Development Speed
Consider your current development methodology. If you are still doing relatively infrequent releases (e.g., quarterly) and have a traditional waterfall-like approach, you might start by strengthening AppSec via periodic reviews and tests.
However, if your team is adopting Agile and DevOps with frequent deployments, you should prioritize DevSecOps practices early. Fast-moving DevOps teams will benefit from automation to avoid security becoming a roadblock. In contrast, a slower-moving team might cope with manual AppSec for a while, but they should still aim to automate over time.
The more your business demands speed and continuous delivery, the more you should invest in DevSecOps tooling and culture to keep up without increasing risk.
Risk Profile and Regulatory Environment
If you operate in a highly regulated industry (finance, healthcare, etc.) or handle very sensitive data, robust AppSec is your ticket for guaranteed compliance. You need to satisfy auditors and regulators in the near term, which means investing in AppSec processes (compliance checklists, documentation, third-party assessments) to meet those obligations.
DevSecOps can absolutely help with compliance, but it might take time to implement fully. So in the short term, prioritize whatever meets your critical compliance needs, likely AppSec measures. However, you should plan for DevSecOps to achieve sustainable compliance.
On the other hand, if your main concern is preventing data breaches and your company has suffered from slow response to vulnerabilities, investing in DevSecOps (like continuous scanning and monitoring) could drastically improve your risk posture by catching issues faster.
Also, consider risk tolerance: if you have low tolerance for security incidents, you will want both strong AppSec and DevSecOps. AppSec to cover known vulnerabilities and DevSecOps to handle unknown or emerging threats swiftly.
Quick Wins vs Long-Term Gains
AppSec investments can yield some quick wins. Running a security scan might immediately reveal a critical vulnerability to fix, thus averting a potential breach. DevSecOps investments are more about long-term gains; it’s about building a robust process that continuously yields benefits.
You should balance both: use AppSec to reduce the chance of costly incidents in the near term, while laying the groundwork for DevSecOps. It will pay off in efficiency and resiliency down the road. For example, you might fund an external app penetration test to get a security baseline (short-term risk reduction through AppSec), and at the same time fund a project to integrate security scanning into your CI/CD (long-term risk reduction and efficiency through DevSecOps).
Measuring Success
Determine what success looks like for both AppSec and DevSecOps in your context.
For AppSec, metrics might be the number of vulnerabilities found and fixed, compliance audit results, reduction in high-severity issues over time, etc.
For DevSecOps, you might track metrics like mean time to detect and fix vulnerabilities, the percentage of build pipelines with integrated security tests, or even deployment frequency (to ensure security isn’t slowing it).
Showing metrics to stakeholders can justify further investment. For instance, if after some DevSecOps improvements you can show that “we’ve doubled our release cadence and cut post-release security incidents by 80%,” that’s a compelling argument that investing in DevSecOps yields value.
Conclusion
AppSec is about deeply securing the code and the application, largely driven by security specialists using testing and best practices. DevSecOps is about weaving that security mindset and tooling into the fabric of development and operations, so security becomes a continuous team effort.
AppSec delivers the “what” (secure code, fixed vulnerabilities, compliance adherence) and DevSecOps delivers the “how” (automated, integrated processes and a culture of shared responsibility).
But perhaps choosing between AppSec vs DevOps is still hard for you. That’s perfectly fine. It’s too much information at once. In that case, why don’t you call our team? Our hiring experts will pre-vet the best IT security analyst of the global talent pool, one who will fit your culture and needs. This expert will make all the best security decisions for your company!
Contact us and let us know more about you!





