Have you ever been a phishing victim? Received an email from your bank (with the logo and everything) notifying you that there’s been unusual access to your account and that you need to verify some details. You go through the link, add your information, and in a matter of days, you find out someone hacked your bank account. It was all a scam! Sadly, there are millions of people that fall for these sketchy emails. And emails are not the only way hackers attack. As time passes by, they are getting cleverer. Now, more than ever, it’s crucial to have top cybersecurity tools to fight against potential attacks.
You might think that you’re not so dumb enough to fall for the typical “I’m the prince of Nigeria and would like to give you 1 million dollars” email, but now, especially during the pandemic, hackers have leveled up their game. Other strategies allow them to steal sensitive data and money from companies and individuals easily.
What is Cybersecurity and Why is Important?
Why is cybersecurity important? – Think of cybersecurity as you think of your house. You don’t let strangers come inside your house, especially when you’re not in it. When you go on a vacation or even to the grocery, you make sure to lock the doors and windows. Cybersecurity is basically locking [protecting] the doors of your devices. It refers to the practice of protecting computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks.
When you don’t have any protection in your devices, you’re the perfect target for hackers. For them, it is as if you have left your house with the doors wide open and a sign that says ‘’come in and take everything you want’’.
But to make it clear, cyberattacks not only come in the form of suspicious emails.
Most common cyberattacks
1. Malware
Malicious software such as spyware, ransomware, viruses, and worms. Once a hacker is inside the system, they can block access to key components of the network, obtain information, install additional harmful software, among other things.
2. Phishing
One of the most common cyber attacks. As mentioned above, phishing consists of fraudulent communications, mostly by email. The usual purpose of this practice is to steal sensitive information such as credit cards or personal information.
3. Denial of service attack
Cybercriminals prevent a computer system from fulfilling legitimate requests by overwhelming the networks and servers with traffic.
4. Man in the middle attack
Consists of a hacker intercepting the communication between two individuals to steal data.
The alarming number of data breaches and information leaks makes you realize the importance of protecting your business and your employees. Now that remote work is the norm, it’s crucial to raise awareness of the importance of cybersecurity.
To realize the magnitude of this issue, here are some stats about cyberattacks:
- Cybercrime increased up to 600% due to the pandemic.
- 47% of remote employees have fallen for a phishing scam.
- Between February and May 2020, more than half a million people globally were affected by breaches in which the personal data of video conferencing users was stolen.
- The global average cost of a data breach is $3.86 million.
- This year, 300 million people have been at risk of identity theft and fraud.
Yes, the numbers are scary. Fortunately, there are great cybersecurity techniques to fight against these cybercriminals and protect at all costs your company’s valuable and sensitive data.
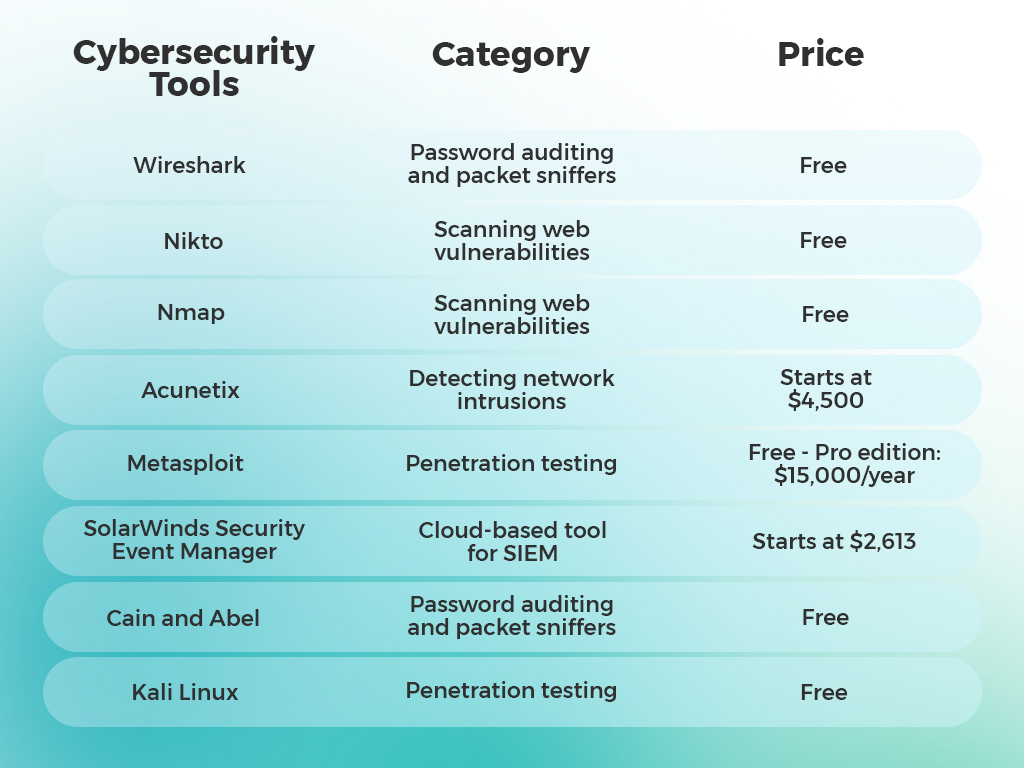
WHAT ARE THE BEST CYBERSECURITY TOOLS FOR 2021? Here’s our list:
- Wireshark
- NIKTO
- NMAP
- Acunetix
- Metasploit
- SolarWinds Security event manager
- Cain and Abel
- Kali Linux
Preventing cyber attacks is not only about telling your team to create stronger passwords. Or to give them a talk about what phishing emails look like. You need to implement software that will act as a repellent from any hacker or cybercriminal. We did the homework for you, and these are the best cybersecurity software solutions for remote work:
1. Wireshark
Wireshark (previously named Ethereal) is a console-based cybersecurity tool. It analyzes network protocols and identifies the presence of potential vulnerabilities. Businesses use Wireshark to watch on network packets and display them in a format that is easy to understand. Overall, it is one of the best cyber attack prevention tools as it helps users understand what’s happening in the network.
Wireshark’s top features:
- Offline analysis and live capture
- Deep inspection of hundreds of protocols
- Captured network data can be browsed via a GUI or via the TTY-mode
- Rich VolP analysis
- It runs on Windows, Linux, macOS, Solaris, among others
Price: Free
2. Nikto
Nikto is an open-source tool used to scan and manage web vulnerabilities; it can detect up to 6700 different types of threats. It checks for outdated versions of over 1250 servers and version-specific problems on over 270 servers. The scans cover mainly web servers and networks, and the database is frequently updated by developers with new thread data. This way, all the new vulnerabilities that might appear on your website are easily identified and managed.
Nikto’s top features:
- Full HTTP proxy support
- Checks for outdated server components
- Save reports in plain text, XML, HTML, NBE, or CSV
- Template engine to easily customize reports
- Mutation techniques to “fish” for content on web servers
Price: Free
3. Nmap
Network Mapper (Nmap) is a multi-platform and open-source cybersecurity tool perfect for scanning networks and IT systems to identify potential threats. It can be used in both large or small networks, and it gives professionals an overview of all the network characteristics. Besides scanning vulnerability, this tool is also about mapping out potential attack surfaces on a network.
Nmap top features:
- It draws a topology map of discovered networks
- Can show the differences between two scans
- Summarizes details about complete scans
- It provides interactive and graphical results
- Administrators can track new hosts or services appearing on their networks
Price: Free
4. Acunetix
Most businesses have web apps or websites to increase their digital presence. These types of sites are often targets of cybercriminals, and therefore protecting them is crucial. Acunetix has the purpose of helping organizations to define defenses for securing their web apps against security threats. It consists of a web vulnerability scanning app (it can detect up to 7000 vulnerabilities) that helps audit the website by discovering potential attacks and bugs like SQL Injection, Email Header Injection, Server-Side Request Forgery, etc.
Acunetix top features:
- In-Depth crawls and analysis
- WordPress checks
- Network scanning
- Assign target management to users
- Vulnerability assessment
Price: Standard plan costs $4,500.
5. Metasploit
Metasploit is a collection that contains different tools mainly for penetration testing exercises. It can test the security of different systems, including web-based apps, networks, and servers, among others. This tool ensures security 24/7, and it’s constantly identifying new vulnerabilities as they emerge. Metasploit also includes automation and pre-written scripts.
Metasploit’s top features:
- Detects system vulnerabilities
- Formulates strategies to concretize cybersecurity defense systems
- Manages security evaluations
- Identifies malicious software that hides to get access
- Helps test deeper penetration in systems
Price: Depends. The community edition is free, but the Pro edition is approximately $15,000 per year
6. SolarWinds Security Event Manager
This cybersecurity tool consists of a network and host intrusion detection system. It performs real-time monitoring and reports potential security threats. SolarWinds Security Event Manager focuses on securing products while increasing the administration, management, and monitoring of your network.
SolarWinds Security Event Manager top features:
- Has inbuilt integrity monitoring
- Find and respond to threats fast
- Offers Log correlation and Log event archive features
- Has an intuitive user interface and dashboard
- It contains integrating compliance reporting tools
Price: Price starts at $2,613
7. Cain and Abel
Oldie but Goldie, Cain and Abel, is one of the earliest cybersecurity tools created to help administrators, analysts, security consultants, among others, to test the security of a network. It works specifically for the Windows Operating systems, and it ensures to discover any weaknesses in the password security systems. It’s the perfect tool for password recovery, and it reveals cached passwords, password boxes, and decodes scrambled passwords.
Cain and Abel top features:
- WEP cracking
- Decodes scrambled passwords
- Uncovers cached password
- Calculates hashes
- Traceroute
Price: Free
Companies using Cain and Abel:
8. Kali Linux
Kali Linux is one of the most popular cybersecurity tools. It consists of an operating system with 600 different tools for security auditing. It adds great value for organizations who want to scan their networks and find out if there are any vulnerabilities in the system. One of the great benefits of this tool is that it can be used by people who are not cybersecurity experts. Users can keep track of the security in their system easily.
Kali Linux top features:
- Multi-language support
- Wide-ranging wireless device support
- Completely customizable
- Developed in a secure environment
- Open-Source Git Tree
Price: Free
Safe and Secure Networks
We can’t make cyber-attacks disappear from the world, but we can install the necessary tools to protect our company from them. These 8 tools have different purposes, but all of them are great options to protect your employees and your client’s data and sensitive information.
However, having a safe and secure network or website requires managing it effectively. And for that, you need an IT professional that makes sure things are running smoothly. If you’re interested in hiring remote tech talent, we can help you! As a remote recruitment agency, we focus on helping companies hire the talent they need. Contact us, and we will help you find a professional who fights against any potential threat your network might face.




