Zero Trust Architecture is a cybersecurity framework based on the core principle of “never trust, always verify.” Unlike traditional models that assume everything inside the corporate network is safe, Zero Trust mandates that no user, device, or application is implicitly trusted.
Think of it like a zombie apocalypse: How do you know if the person entering your home is about to become a zombie? How do you know if that person is who they claim to be? Whatever your method is, you shouldn’t trust them at face value. In the digital world, Zero Trust Architecture applies the same scrutiny to every single access request, regardless of its origin. Is a technical design principle summarized as “never trust, always verify”.
No user, device, or application should be implicitly trusted to access company resources, even if it’s already inside the corporate network. Every access request must prove its legitimacy.
Finally, a Zero Trust architecture designs and configures security in networks, VPNs, and identity systems, but not how we treat our colleagues on a personal level. Zero Trust is about how we approach devices and cybersecurity, not about being suspicious and distrustful of others.
We will explain what ZTA is (and isn’t), provide examples of it in action, and show how you can enforce Zero Trust principles in IT while still fostering a high-trust, collaborative workplace culture.
What Is Zero Trust Architecture (In Plain English)?
Zero Trust Architecture means: never trust, always verify. Instead of trusting anything just because it’s “inside the network,” Zero Trust treats every request as potentially hostile, whether it comes from:
- Inside or outside the company
- Remote access from an employee or a contractor
- A laptop in the office or a cloud workload
Access decisions are made dynamically based on:
- Identity (who or what is requesting access)
- Device posture (is the device secure and compliant?)
- Context (location, time, risk signals)
- Least privilege (only what’s needed, nothing more)
Think of it less like a castle with walls and more like a hotel with keycards that expire and update constantly.
Therefore, being on the internal network no longer gives a free pass. Every user and device must continuously earn trust through verification.
Why Traditional Security Fails Modern Organizations
In traditional “castle-and-moat” security models, anyone on the inside of the network (inside the moat) was automatically trusted. Traditional security models assume the internal network is safe and secure, and that defenses against hackers are enough. Once logged in, users can move freely. However, what if an attacker passes the firewall or a rogue insider is already inside? They will obtain free rein to move through the network and access sensitive data.
With data and services spread across cloud providers, remote work becoming common, and sophisticated breaches on the rise, common defenses alone are insufficient. Companies can no longer assume “inside is safe”. A Zero Trust architecture instead verifies every access and limits what each user or system can do, greatly reducing the damage if an attacker does get in.
Zero Trust Architecture Is Not “Zero Trust in People”
This is where many leaders hesitate. Zero Trust does not mean micromanaging employees, distrusting teams, or slowing work with constant approvals.
Instead, it does mean trusting people without trusting assumptions, removing implicit access, and making security predictable and fair.
In high-trust cultures, expectations are clear. A Zero Trust architecture does the same for systems: “Here’s what you can access, why you can access it, and under what conditions.”
This clarity reduces friction, not increases it.
In short, “Zero Trust” in IT does not mean you should have zero trust in your employees or cultivate a cynical workplace. The Zero Trust Architecture is about technological trust (or the lack thereof), not personal trust. In fact, if not communicated carefully, a strict Zero Trust security rollout could inadvertently send the wrong message to staff.
Your firewall should trust no one. Your manager should trust everyone, fostering a high-trust culture among people.
5 Key Principles of Zero Trust Architecture Implementation
Zero Trust is not a single product or one-time fix, but a set of guiding principles and technologies. Here are the key principles and how to implement them in your company.
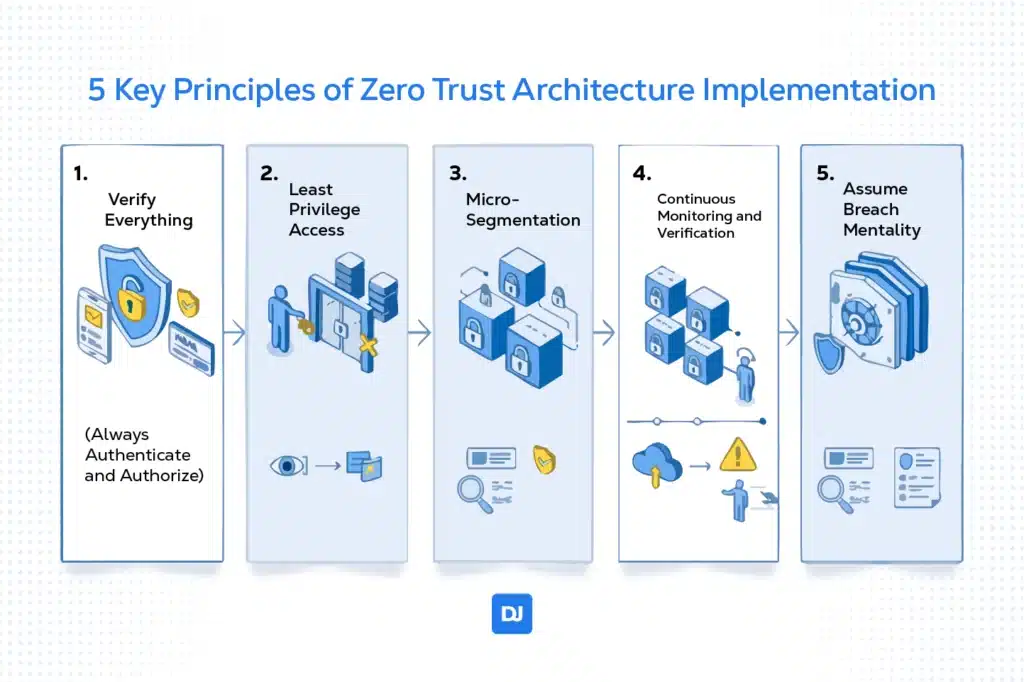
1. Verify Everything (Always Authenticate and Authorize)
Every access request is validated in real-time. No user or device is exempt from proving who they are and that they have permission for what they’re trying to do, whether they’re connecting from inside headquarters or from a home office.
For example, strong identity checks such as multi-factor authentication (MFA) for users, and verifying device identity or health status for machines. In practice, even if you’ve logged into the network, accessing each application or dataset may require confirming your identity and device again. “Never trust, always verify” is enforced at each step.
2. Least Privilege Access
Users and services get only what they need, for only as long as they need it. By limiting privileges, a Zero Trust Architecture ensures that even if an account is compromised, the damage is contained.
For example, an employee in accounting shouldn’t have access to software development servers, and vice versa. Users get only the keys and access they need rather than a master key to the whole network. Doing so, a breach of one account doesn’t automatically open up everything else.
3. Micro-Segmentation
Zero Trust breaks the traditional flat network into smaller zones or segments. Sensitive resources are isolated, and fine-grained access rules govern traffic between segments. Even if an attacker breaches one part of the network, they cannot easily move laterally to other systems.
Imagine it’s like having many locked rooms inside a building instead of one big open floor. Breaching one room doesn’t open all doors. Network segmentation (down to micro-segmentation of individual apps or workloads) limits how far an intrusion can spread, minimizing the “blast radius” of any incident.
4. Continuous Monitoring and Verification
Zero Trust isn’t a one-and-done checkpoint. Instead, it involves continuously watching and re-evaluating trust. Even after access is granted once, the system keeps an eye on user behavior, device health, and other signals to detect anomalies.
If something seems off, Zero Trust systems can revoke access or require re-authentication. For example, let’s say a user account suddenly downloads massive amounts of data at 3 AM, or a device shows signs of malware.
This ongoing verification is akin to airport security checking your boarding pass at multiple checkpoints. It’s not to hassle you, but to catch inconsistencies or threats that might appear later in the session.
5. Assume Breach Mentality
Here’s a subtle, but important, mindset in a Zero Trust Architecture: assume that a breach may have already occurred or will occur, and design controls accordingly.
Prepare for the worst: monitor internal traffic for malicious activity, keep detailed logs, and have incident response plans ready. Assume any component might be compromised. In that way, you proactively build layers of defense that can detect and contain issues early.
In other words, “trust no one, including those inside the house, because they might have been compromised.” This principle drives organizations to encrypt data, employ robust intrusion detection, and require verification even for internal system-to-system communications.
Business Benefits of Zero Trust
Zero Trust might sound abstract, but many companies have already implemented it with several benefits. Zero Trust is not a “security tax.” It’s a risk and efficiency strategy. Here are a few examples that illustrate Zero Trust Architecture advantages.
Reduced Breach Impact
Even if credentials are stolen, attackers can’t freely move or escalate the threat. Thanks to the Principle of Less Privilege, they are only allowed to do what their credentials permit.
Faster, Safer Scaling
If you are hiring globally or have onboarding contractors, Zero Trust makes access temporary, auditable, and reversible. In that way, your system is safer.
Better Compliance Posture
Zero Trust aligns naturally with many laws:
- SOC 2
- ISO 27001
- HIPAA
- GDPR
And auditors love explicit access controls and logs. A Zero Trust Architecture naturally brings compliance!
Trust Through Transparency
Employees know what they can access, why they have access, and how access may change over time. This clarity supports psychological safety and accountability.
Zero Trust in Action: Real-World Examples
Zero Trust is not a single product. It’s an architecture implemented by the biggest companies in the industry. Here are a few examples and scenarios that illustrate Zero Trust Architecture in practice.
Google’s BeyondCorp (Eliminating the VPN)
Google is one of the earliest large-scale adopters of Zero Trust, through its BeyondCorp initiative. The company found the traditional approach (where employees outside the office had to VPN into a trusted network) both cumbersome and risky.
In 2011, Google faced large attacks and reimagined its security using Zero Trust principles. Under BeyondCorp, being on Google’s corporate network does not automatically grant access to services.
Instead, access is determined by what is known about the user’s identity and the device’s security posture, and all access to services must be authenticated, authorized, and encrypted for every request.
Every Google employee can work from an untrusted network (like home or a coffee shop) without a traditional VPN, because each time they access an internal application, the system verifies who they are and checks that their laptop or phone is a trusted, secured device.
This transition improved security (no more implicit trust for insiders) and made life easier for employees, who no longer have to jump through VPN hoops to get their job done.
Government Adoption
Zero Trust is becoming standard practice in government and other sectors. For example, the U.S. federal government has mandated agencies to adopt Zero Trust architectures to better protect national data. An Executive Order in 2021 required all federal agencies to develop plans for Zero Trust, and the Department of Defense released a detailed Zero Trust roadmap that its contractors must follow.
High-profile breaches of government systems drove this push. It reflects a consensus that “never trust, always verify” is now essential for cyber defense.
Enterprise Case (Cimpress)
Many enterprise businesses are on the same path. As a broader case study, Cimpres (a global printing company with 16,000 employees) embarked on a Zero Trust transformation to secure its diverse subsidiaries.
Cimpress’s security team implemented measures to check “every access request for valid authentication and authorization, implement least privilege access controls, reduce reliance on perimeter-based controls… and implement segmentation” across their corporate systems.
This change required updating processes and technology, from deploying MFA company-wide to segmenting cloud workloads. While it was a multi-year effort, the outcome was a markedly improved security posture and faster detection of suspicious activity. Cimpress noticed that as they rolled out Zero Trust controls, their security team’s mean time to detect and contain incidents dropped significantly.
In other words, attacks that might have gone unnoticed in a traditional network were quickly spotted and isolated under Zero Trust. This case reinforces that Zero Trust Architecture is effective not only for tech giants or government agencies, but for any company that needs to protect a complex, distributed IT environment.
Conclusion
A Zero Trust Architecture is a powerful framework to secure your business’s IT systems in an age of cloud computing and relentless cyberattacks. You can redesign your security so that nothing gets a free pass; every user, device, and access request must continually prove itself trustworthy.
As we’ve discussed, this involves tools like identity management, endpoint verification, and network segmentation, all working together to limit damage and never rely on implicit trust. Adopting Zero Trust can greatly reduce the risk of data breaches and unauthorized access. It enables more flexible work arrangements because security is tied to users and devices rather than physical offices or network segments.
If you have decided to take a step towards a safe Zero Trust Architecture, we provide you with both developers and cybersecurity professionals who pass the strictest security standards, so you can stop micromanaging and start collaborating. Call us today and get the best cybersecurity staff for your business!





